I had a WordPress incident
Kamil Senecki | 2024-04-16The threat is closer than you think
In the era of AI and digitization, new products are continuously hitting the market. Despite many initiatives being taken by specialists and researchers around the world, the topic of network security is often further downplayed in many companies for various reasons.
The main reasons are costs and gullibility. Implementing robust security solutions can be expensive, both in time and money. Moreover, many people may simply assume that their websites are not at risk of attack or that they are not important enough to be a target for cybercriminals. This thinking, combined with high costs, often leads to vulnerabilities and incidents.
Many people are not aware of the variety of threats that may occur in cyberspace. Lack of awareness of attack methods and the consequences of insufficient security may lead to neglect of security issues. Additionally, some people consider security to be less important than other aspects of a website, such as appearance, functionality, or accessibility. As a result, they may take risks by sacrificing appropriate security measures to achieve other goals.
Cybercrime grows and becomes more advanced so more and more people realize the need for an appropriate level of security for their applications. Implementing proper security practices is becoming more common, and awareness of how important website security is growing as well. However, nothing helps to increase the safety budget like an incident in production.
How it started
It was the first half of 2023, as we were approached by an international company that wanted to conduct a security audit of a website built on WordPress. The case was very important to them because the image and well-being of customers were at stake. Our team performed a series of tests that revealed a few potential but harmless vulnerabilities, most of which could be patched by updating the website engine and all plugins on it. Tests completed, report accepted, topic closed.
That’s what we thought.
The client contacted us a year later asking for intervention. There was malware on the website and a scan was performed using the website https://scanner.pcrisk.com/ revealed that something was not ok.
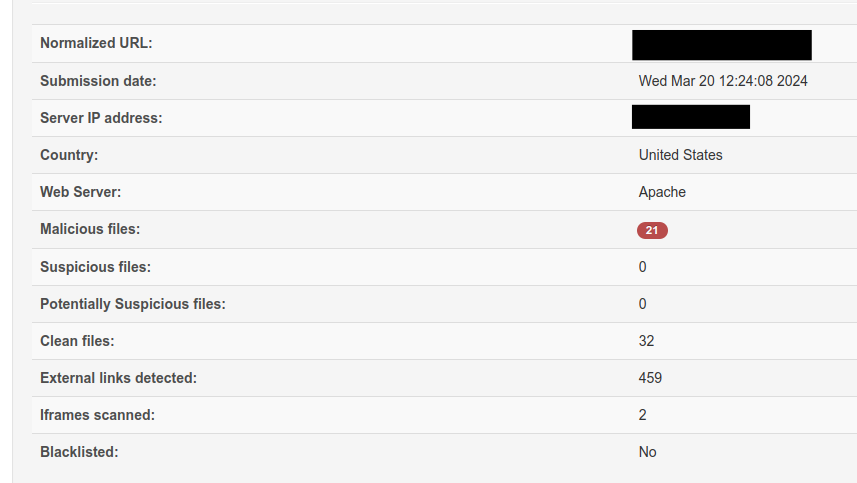
It was not a game changer, but enough to make them think about potential risk. We decided to log in to the administration panel and see what the situation was like. It turned out that both the WordPress engine and all plugins needed updating.
To speed up the entire process, we decided to update all plugins at the same time. This resulted in the server running out of RAM immediately. The website stopped responding and the server returned http error 504. A quick restart of the AWS machine and we were back in the game.
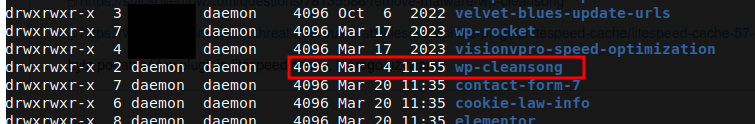
While searching the Internet, we came across an interesting article on one of the Chinese websites about WP-Cleansong malware, the behavior of which looks like what we observed on our client's page. Indeed, among the installed plugins there was the one mentioned. It was present in the plugins directory, not in the wp-admin view.
Cybercriminals never sleep
It turns out that the malware exploits a vulnerability in the LiteSpeed Cache plugin, which was installed on the website. However, this shouldn’t be the case, because the plugin update from 25.10.2023 patched the vulnerability, and the file creation date clearly showed that the malware was installed on the website on 4.03.2024.
The explanation is very simple. The plugins were updated right after we audited the website, and then the site was left as it was. No one had any interest in it. The incident was the result of an automated script scanning the Internet for vulnerabilities and exploiting them.
Our team ultimately identified the following impacts:
- wp-blog-header.php core WordPress file modification
- two admin users created: wpsupp-user and admin[@]zzna[.]ru
- wp-cleansong plugin installed (not visible from the WordPress plugins page, but it existed in the /plugins folder)
The solution was simple:
- wp-cleansong: delete the plugin folder manually through FTP or SSH
- delete unauthorized admin users
- wp-blog-header.php: replace the file manually
Our recommendations:
- reset admin passwords
- change the database password (change it in wp-config as well or you'll have a white screen of death)
- change cpanel (or hosting) access passwords
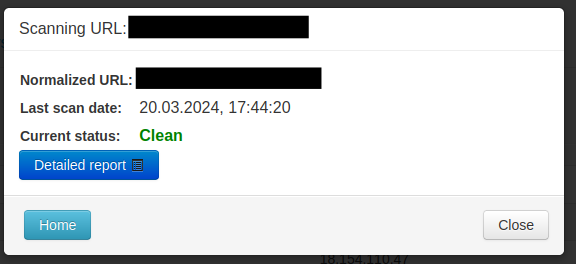
A rescan of the website using appropriate applications confirmed that the malware had been removed. The website engine and all plugins have been updated.
Events timeline
- The customer asks us to audit his WordPress website.
- We check the mentioned website security and give recommendations.
- 6 months later customer asks for help again. This time there is malware on his website.
- We fixed the website and gave recommendations.
Lessons learned
Many attacks on WordPress-based websites result from the exploitation of security vulnerabilities and plug-in vulnerabilities. Regular updates help protect the website and prevent cybercriminals from exploiting vulnerabilities. Attacks on websites can lead to various financial and image consequences. We may lose data, and customers and generate more additional costs.
This time, the losses were minor and the incident focused management's attention on safety, helping the company avoid more serious problems in the future.
Let's take care of cybersecurity together.
